Most Data Leaks Start With a Missing Filter
If you're building a modern software-as-a-service (SaaS) application, especially one that serves multiple companies or users from a single database, you've likely had a cold sweat moment. That moment where you wonder: Is it possible for Tenant A to accidentally see Tenant B's sensitive data?
Look, if you run a multi-tenant app, keeping one customer's data away from another's isn't optional—it's the absolute, non-negotiable rule. Messing up and mixing data is basically a disaster that could shut your business down.
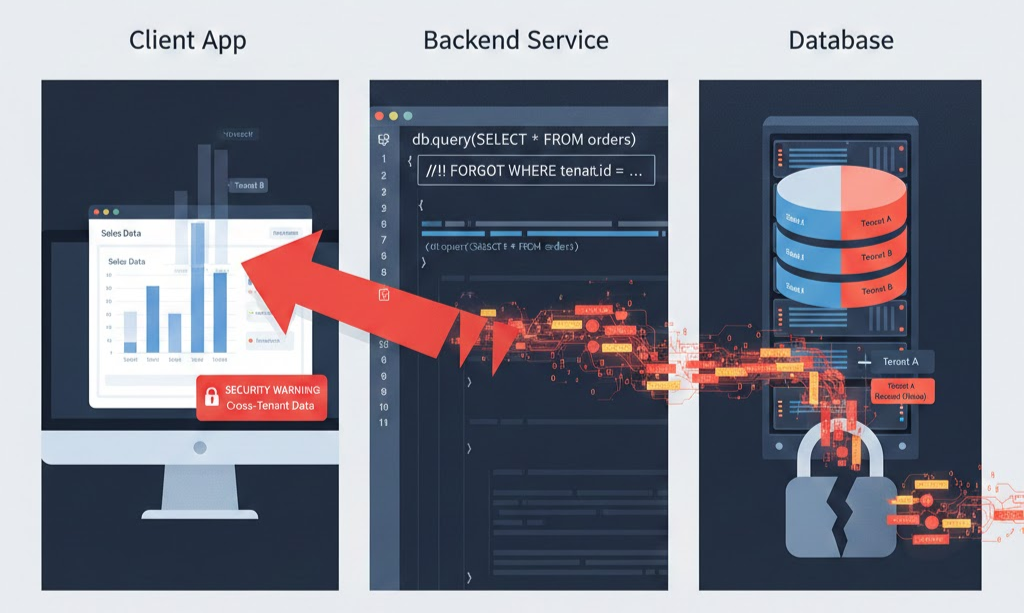
The underlying problem RLS solves is the fragility of application-level filtering. We spend countless hours writing application logic to filter queries with WHERE tenant_id = current_user_id. However, this is a Soft Security Boundary because it relies on human developers to be perfect 100% of the time, in every single API endpoint and microservice. A single missing WHERE clause is a massive data leak.
RLS exists to provide a Hard Security Boundary right at the data level, solving this systemic vulnerability by shifting the responsibility from fallible human code to the robust database kernel.
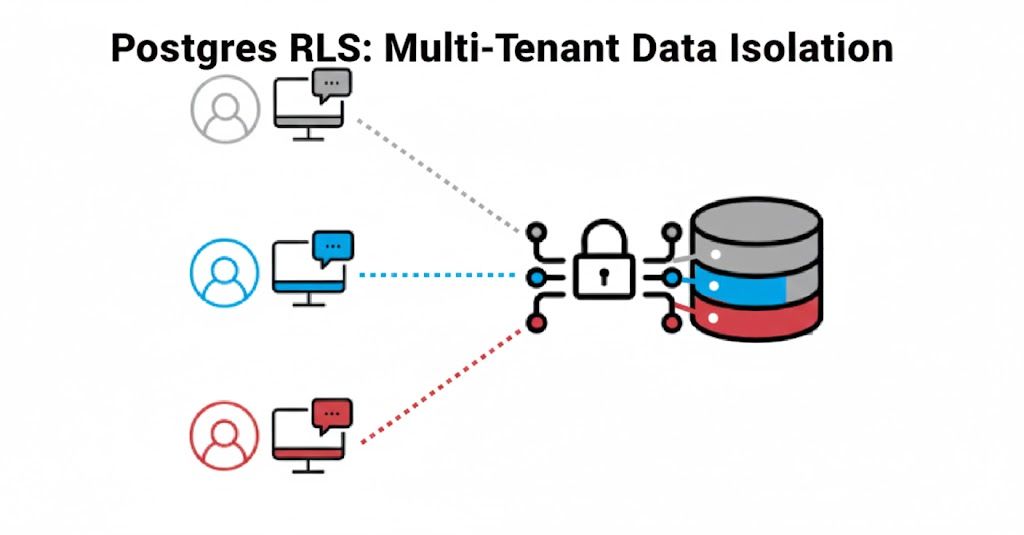
Meet RLS: Your Database's Invisible Force Field
This is where PostgreSQL's Row Level Security (RLS) steps in. The core purpose of RLS is to enforce those hard boundaries using a database-level mechanism that provides fine-grained access control by automatically filtering the rows a user can access in a table.
How RLS Solves It
The goal of RLS is to ensure mandatory filtering. When your application, running under a specific database role, sends a general query like SELECT * FROM customer_data;, RLS doesn't just process it as-is. Instead, it acts as an invisible Query Rewriter.
- Intercept: RLS intercepts the incoming query.
- Apply Policy: It identifies the active policy rules (e.g., "only show rows where
tenant_idmatches the current session's tenant ID"). - Rewrite: RLS internally rewrites the query before it hits the storage engine. The database effectively executes:
SELECT * FROM customer_data WHERE tenant_id = [current user's tenant ID]; - Execute: The storage engine only processes and returns the subset of data the user is authorized to see.
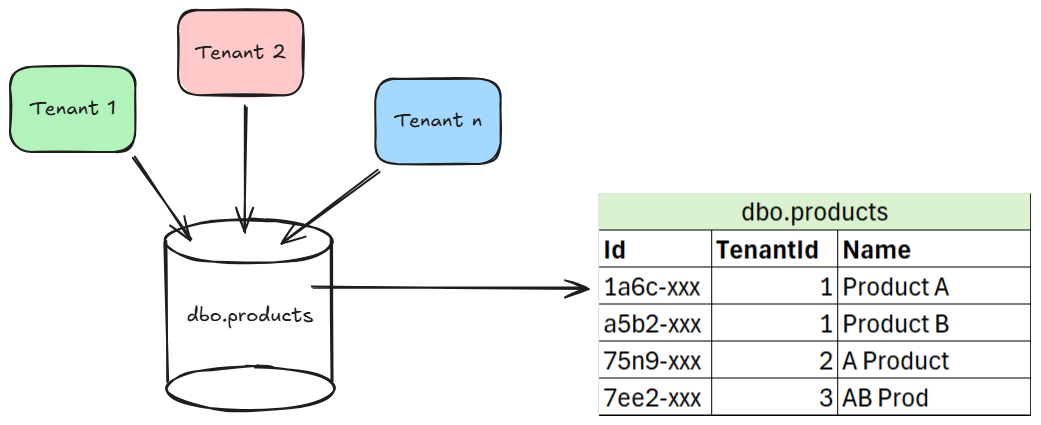
The best part? It's transparent to your application. Your code can query the whole table, but the database will only ever return or affect the rows that the current user is authorized for. RLS becomes the technical backbone of your promise of data isolation.
How to Lock Down Your Data
Implementing RLS is surprisingly straightforward. You need two main things:
- Enable RLS on the table:
ALTER TABLE dbo.products ENABLE ROW LEVEL SECURITY;2. Create the Policy: This is the rule that defines the boundary.
For a simple multi-tenant setup, the policy usually looks like this, relying on a session variable to identify the current user's tenant:
CREATE POLICY tenant_isolation_policy
ON dbo.products
AS PERMISSIVE
FOR ALL
USING (tenant_id = current_setting('app.current_tenant')::integer);This policy ensures that for all commands (FOR ALL), the database will only consider rows where the tenant_id matches the session variable we set when the user connects. You can even have granular policies, like a PERMISSIVE policy for reading data and a more RESTRICTIVE policy for deletion.
The Challenges You Must Face
RLS is powerful, but it's not a silver bullet. When you push security to a lower layer, you inherit some complexity. Here are two of the biggest "gotchas" developers run into:
The WITH CHECK Headache (Security Leaks)
A common mistake is forgetting that a policy needs to govern both what you can see (USING) and what you can create/modify (WITH CHECK).
For example, if you only define the USING clause, a malicious user might be able to INSERT a new row and set the tenant_id to Tenant Z (a tenant they don't belong to). Since their read policy prevents them from seeing Tenant Z's data, the insert seems successful but the data is now inaccessible to them—and it has been injected into another customer's space!
Global Context Management
RLS relies on knowing who the current user/tenant is. We typically do this using session variables, like SET app.current_tenant = 'X'.
The challenge is operational: You must ensure that this context variable is set reliably and immediately at the start of every single database transaction, and that it's cleared or reset correctly when the transaction finishes. In highly concurrent environments with connection pooling (like pgbouncer), managing this context correctly is a major source of subtle, hard-to-debug bugs. If the context leaks between connections, so might the data.
Conclusion
Row Level Security is the foundation for building truly secure, multi-tenant applications in PostgreSQL. It simplifies your application logic by offloading critical security responsibility to the database.
While the "Complexity Tax" involves careful handling of WITH CHECK and reliable context management, these challenges are absolutely manageable if you approach them with discipline and robust testing. Use RLS to clean up your codebase and give yourself (and your customers) peace of mind!